Map Of Cybersecurity Domains
In the ever-evolving landscape of cybersecurity, understanding the various domains can mean the difference between a well-fortified digital fortress and a precariously weak one. Mapping out these domains not only clarifies their interrelationships but also illuminates the myriad challenges faced by organizations striving for robust security.
Cybersecurity Domains Mind Map – Version 1
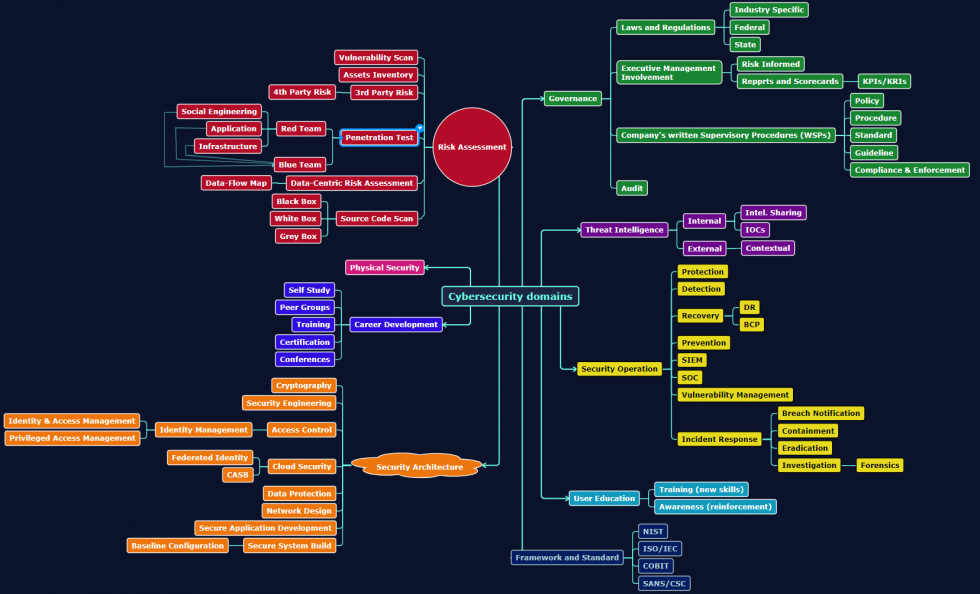
This intriguing mind map elucidates key cybersecurity domains, allowing one to visualize concepts such as risk management, incident response, and data protection. Each domain weaves a complex narrative of its own, presenting unique challenges that cybersecurity professionals must navigate.
Map Of Cybersecurity Domains – Visual Overview
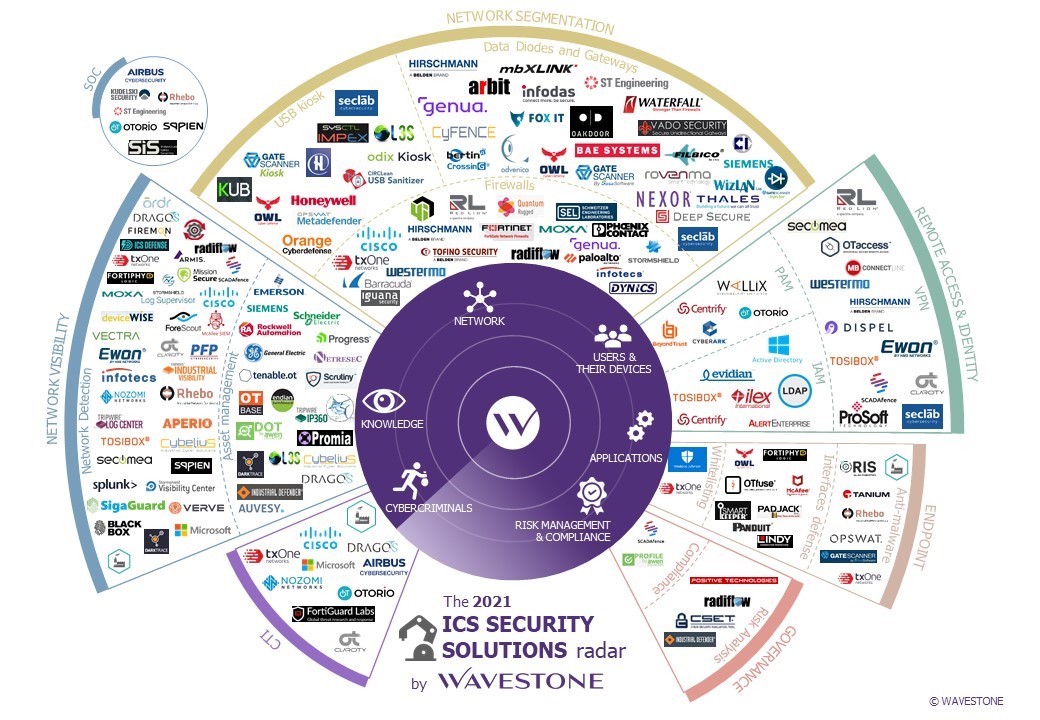
The vibrant colors and structured layout of this map facilitate comprehension of how these domains interact. It serves not only as a reference guide but also as a source of inspiration. The interplay between domains is akin to a carefully orchestrated symphony, where each musician contributes essential notes to the overarching composition.
Cybersecurity Domains Mind Map – Version 2

Here lies another perspective on the cybersecurity framework, showcasing domains such as governance and compliance. Emphasizing the dynamic tensions among them presents a thought-provoking examination of how one domain’s virtues can sometimes contrast sharply with another’s vulnerabilities.
Cybersecurity Domains Insight

This image encapsulates the essence of a comprehensive cybersecurity strategy. Highlighting the importance of staying ahead of cyber adversaries, it encourages continuous education and proactive measures. Each domain is a vital cog within a larger machine, underscoring the necessity for integration and synergy.
Yet Another Cybersecurity Domains Mind Map

As this final visualization indicates, the landscape of cybersecurity is multifaceted and intricate. It offers a profound understanding of the importance of aligning technology, processes, and people to safeguard organizational assets against threats. The map beckons stakeholders to reflect on their current security postures and to uncover areas ripe for enhancement.
